This article is about adding Azure Active Directory to a Function App. The same principles could be applied to an Azure Web App as this concept is for any Azure App Service.
In addition to securing a Function App via OAuth, I have the requirement that the secured Function App be called from another Function App. This means the calling Function App will need to run as an application identity, instead of as a user’s identity.
Why aren’t you simply using Authorization Keys?
According to Microsoft’s docs:
While keys may help obfuscate your HTTP endpoints during development, they are not intended as a way to secure an HTTP trigger in production. To learn more, see Secure an HTTP endpoint in production.
Specifically, this article details the first option in the Secure an HTTP endpoint in production link. This blog post attempts to simplify some of the documentation Microsoft has provided.
Set up in the Azure Portal
- In the Azure Portal go to the ‘Platform Features’ tab of your Function App.
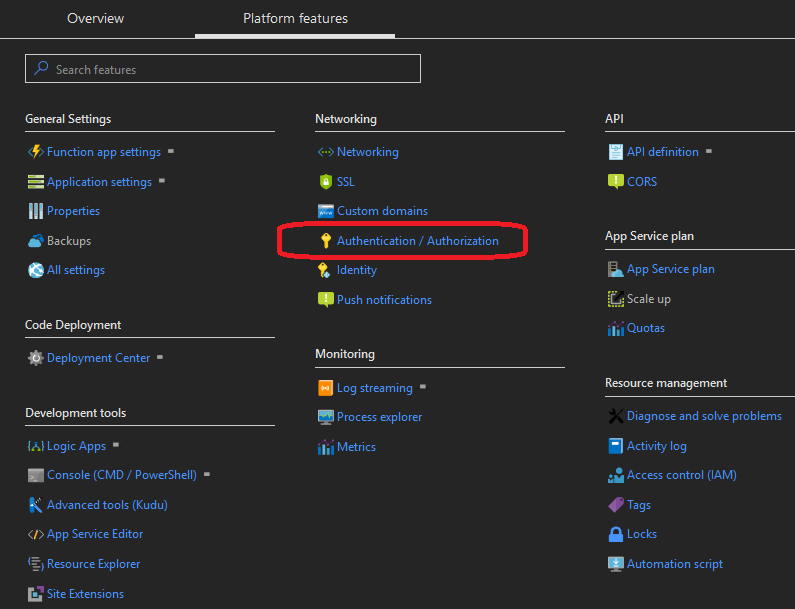
Click the ‘Authentication / Authorization’ link (in the ‘Networking’ section)
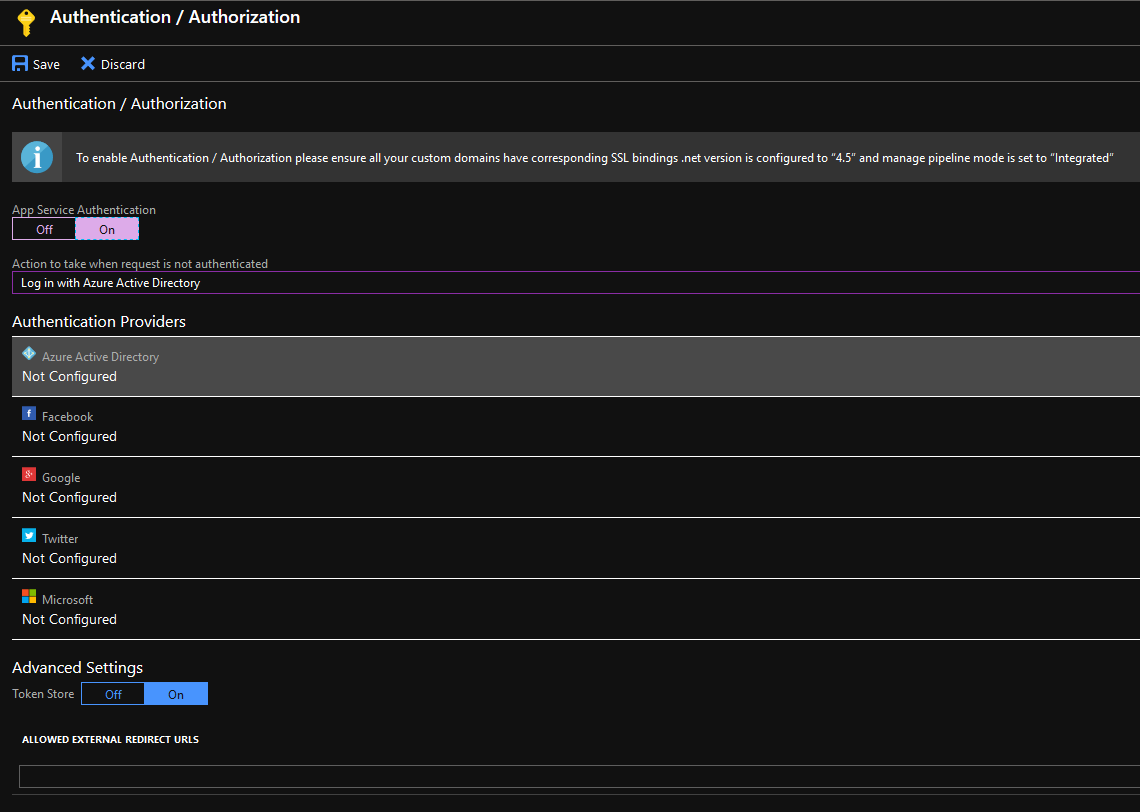
a. ‘App Service Authentication’: ‘On’
b. ‘Action to take when request is not authenticated’: ‘Log in with Azure Active Directory’
c. ‘Authentication Provides’: ‘Azure Active Directory’
i. 'Management Mode': 'Express' ii. Leave the defaults and click 'OK'
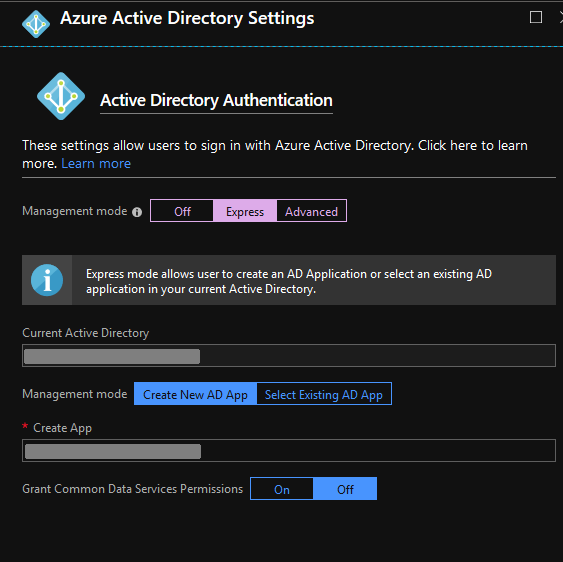
- In the portal go the ‘App Registractions (Preview)’ tab of ‘Azure active Directory’
- From the ‘Own applications’ tab select the application that you just created - this should have the same name as the App Service.
- Click the ‘Certificates & Secrets’ tab
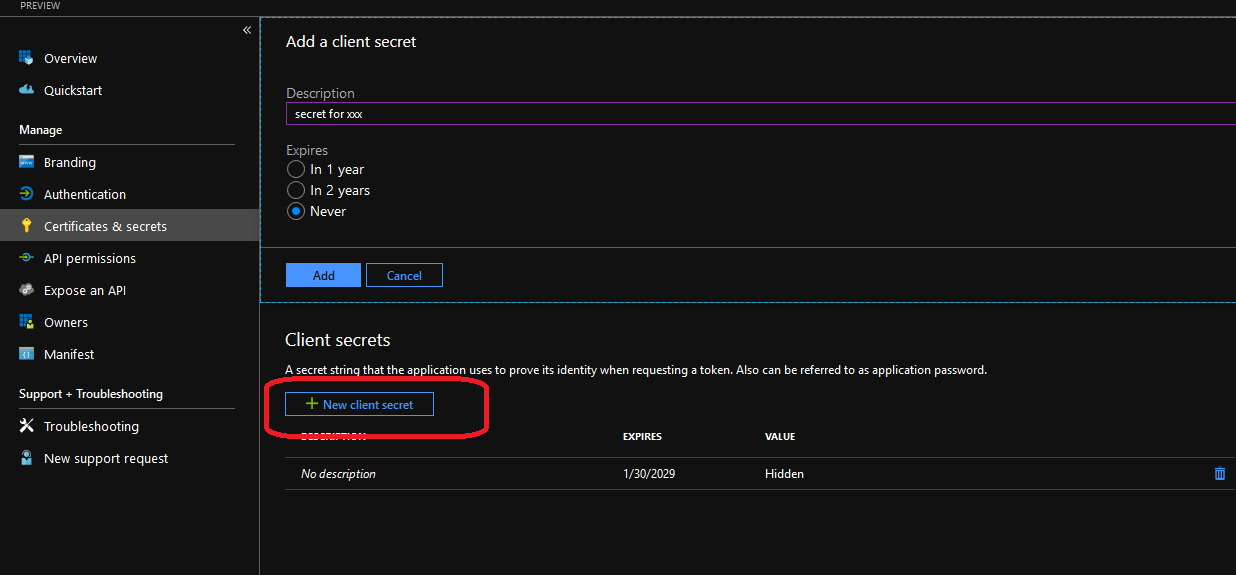
Click ‘New client Secret’ button:
a. Give the ‘Description’ a meaningful name
b. Choose your expiry.
c. Click Add
d. Note down the new client secret value, as it is only shown until you leave this blade in the Portal. I recommend story this directly into Azure KeyVault for future use.
Testing with a User Identiy
In your browser, when you navigate to the Function App’s URL* you should be re-directed to login via Azure Active Directory. After authenticating should be re-directed to the homepage which tells you the Function App is up and running.
*You can get your Function App url from the Azure portal, by going to your Function App and clicking the URL link.
Testing with the Client Secret
We can now peform a FormUrlEncoded HTTP Post to https://login.microsoftonline.com/{AzureActiveDirectoryTenantId}/oauth2/token to get a bearer token:
From here you can wrap the bearer token in a AuthenticationHeaderValue and add it to the Authorization property of your HttpClient’s DefaultRequestHeaders:
var token =
await _azureAppServiceAuthenticator.GetBearerToken();
var header = new AuthenticationHeaderValue("Bearer", token);
HttpClient.DefaultRequestHeaders.Authorization = header;